I’m forced to write another article about XPrivacyLUA because the developer M66B decided to answer me with even more false information in his own XDA thread. In other words, he claimed my previous article – or parts of it – are wrong. Marcel Bokhorst reacted in order to correct my statements I did in my article. He decided to go the ‘bitch way’ which means instead of leaving a comment on my Blog article or trying to contact me directly he simply wrote it into his thread, as a result I get the consequences which force me to debunk some ‘privacy’ myths and comment on his ridiculous tries to defend a weak module.

Never say something about any application when fanboy’s are involved
I posted an article about Xprivacy LUA several days ago (5 April) and it seems the author or the community disagree with my article, as result, I got massive spam in my eMail P.O. Box. I I also got several eMails which threating my life which is a whole new kind of level.
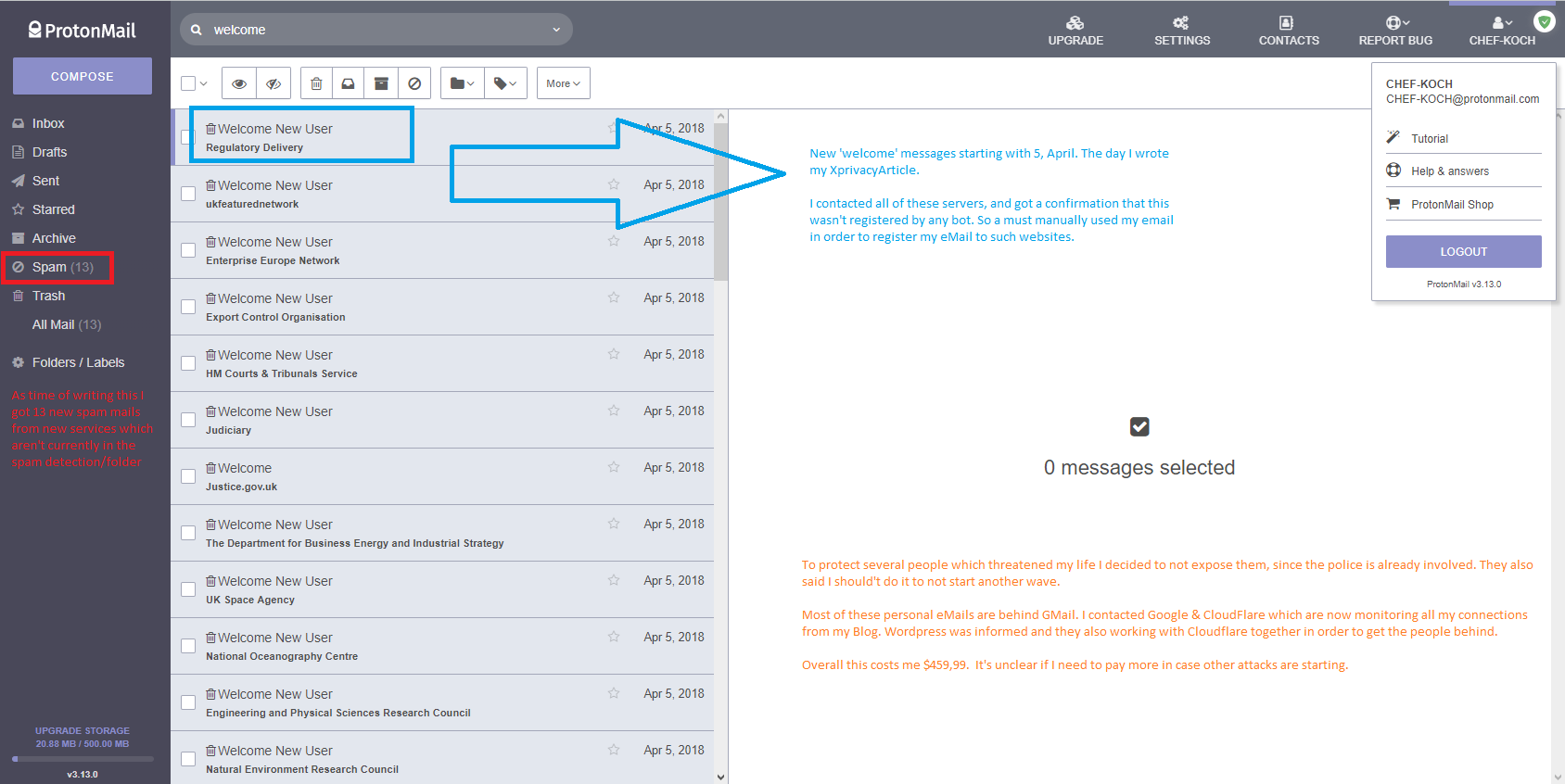
Which only shows yet again that some people have huge problems in case you criticize their loved product. I remember years ago when I exposed some Kaspersky, Avast & Norton holes the same thing happened (except the threats on my life). I’m in general a controversial person, which I not like to hide, this is shown last year on Guru3d.com after the mod/developer refused to answer my open course question or provide any evidence. Read the full story here. As a result I got a permanent ban from the developer of MSIAfterburner. I leaked his source code later on GitHub (invisible) in order to debunk some of the lies. However, it’s not new that people trying to suppress me or trying to destroy my reputation but since I got several serious threats on my life I decided to involve the police.
XPrivacyLUA – Marketing lies at his best
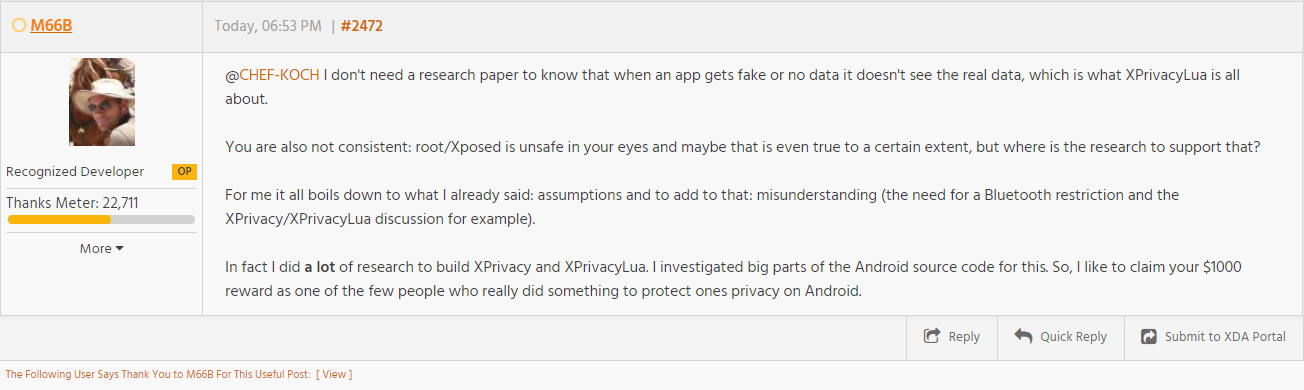

His FAQ mentioned some drawbacks, like that it’s still possible that the app crashes, while this isn’t directly visible on the front page or the Repo. In fact it’s not really visible that this has some limitation, instead the links to a FAQ which get’s updated here and then. The mentioned things on the XDA front page are incorrect, not proven and FUD.
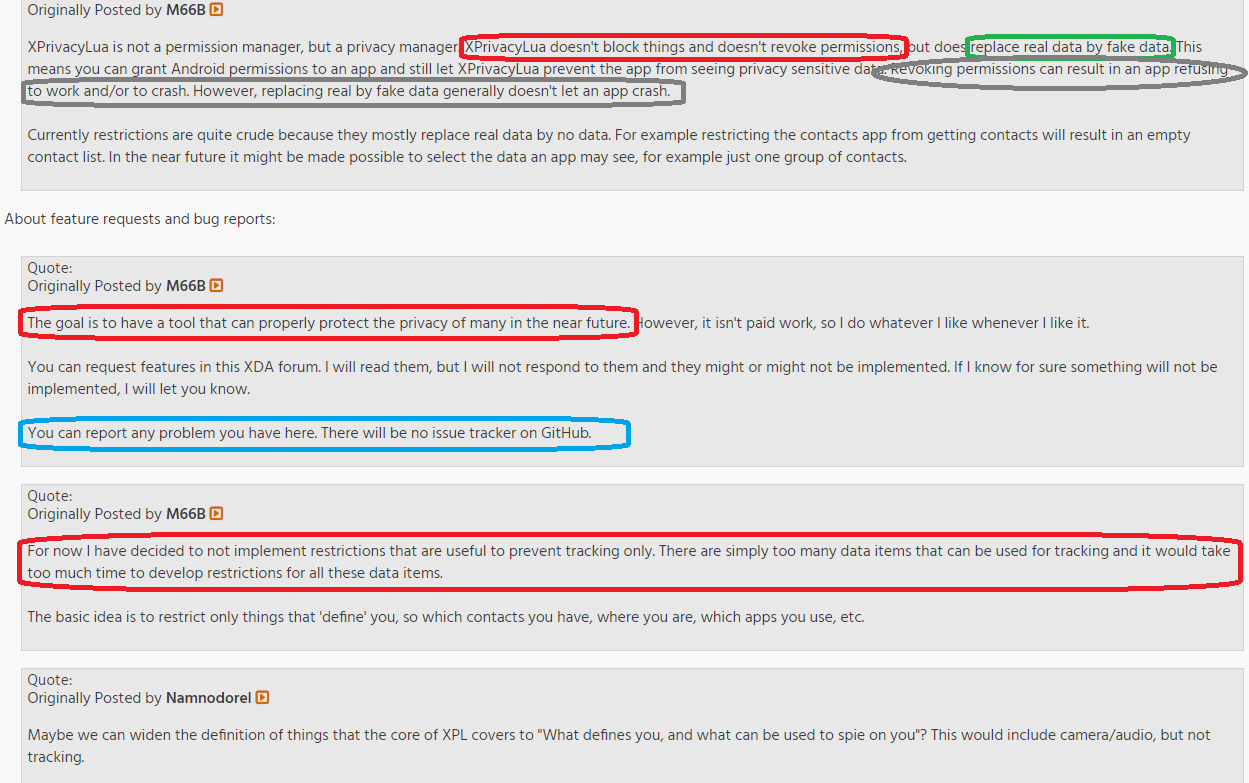
The inconsistence is that the frontage doesn’t mention how ‘Namnodorel’ fits into the project doesn’t tell it if he is involved to speak in M66B name or another developer. When you argue about the red marked things you get back ‘it’s not what you think it is’ even if the front page clearly wrongly advertise this as ‘tool’ (it’s not even a tool btw) that can properly protect your data. It’s unclear what is mean by ‘real data’ and the overview page on GitHub or the XDA thread mentioned which data are ‘real’ and if it covers metadata, protocol-related data, user data or not.
The slogan ‘if you value your data’ is the same marketing lie which the AV industry want to make us believe in order to buy the products. Speaking about buying something, you need to buy the pro version in order to use XprivacyLUA full ‘power’. Which mean defining additional or custom hooks.
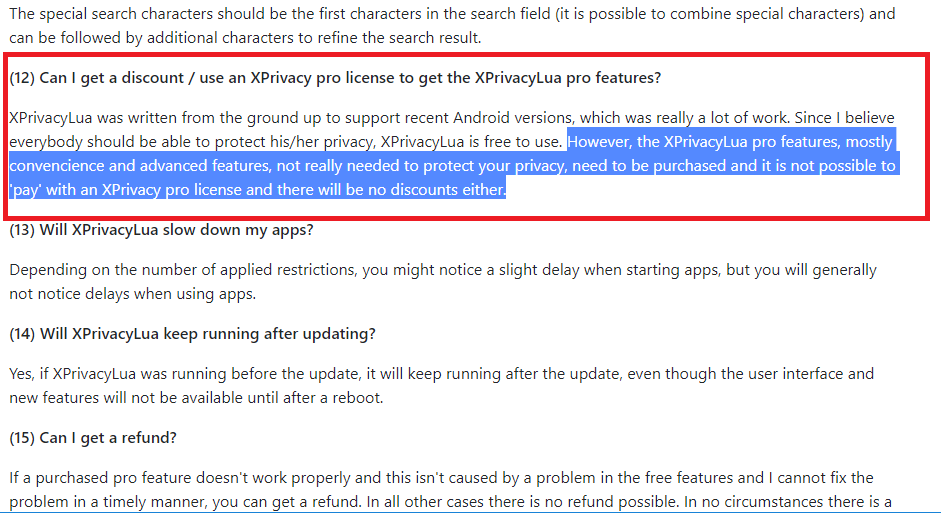
The user Namnodorel in meantime started to defend M66B product in order to make it, even more, worse, see here or when he tried to answer in M66B name here. I answered most of his stuff and corrected his believes. This user also tried to explain me basic things about root, which was irrelevant and also wrong.
The real reason why Bokhorst coded another tool instead of implement XprivacyLUA functionality into it’s existent app
According to Bokhorst, Google removed XPrivacy from the Android Play Store soon after it was made available. But the store still includes a tool that will at least walk you through the installation of the app. Not being in the Play store makes it harder for Bokhorst to sell the tool, but that doesn’t bother him.
He’s not building the tool for money. “The goal of the XPrivacy project is to offer a free, decent Android privacy solution for as many as possible people,” he says.
Merging and using the existent code with LUA would be possible, no matter if the developer says he doesn’t want it or not, he could have used Xprivacy’s code and the database he got from his crowd. Instead, he coded a new one, maybe in order to get money since Google blocked him. he never gave any real explanation why he let his Xprivacy community hang, instead, he decided to advertise a new product as successor.

I question here if someone codes without everything in mind (aka money), since we all have to pay our bills so how does M66B survive if it doesn’t ‘bother’ him? Can we believe a liar? I also can officially pretend I did not code for money, but it would be a lie, cause I need some money in order to pay my debts etc. If he does not need money why provide a pro version? Just give the entire app for free from the beginning if this isn’t an argument. People still could donate M66B anyway.
It’s also unclear what the developer really does with the collected data from Xprivacy. Some ‘bad’ guys theoretically can use this information in order to build strategies to defeat such apps. It’s also possible to sell those data, which is unclear.
I don’t see any information which are really from importance, except curious options, donation buttons and more questions than answers.
Credibility from someone which don’t know much about ‘privacy’ related topics or how to comment on my Blog
I question M66B credibility, he already lied when he said he tried to contact me. What he said here is just a lie and not true, my Blog log doesn’t list any effort to contact me, besides I provide several other ways to contact me which do not require any registration. Even if there would be a mysterious bug which only M66B forced to ‘login’ in order to comment, there were enough other options. The entire story that he tried to contact me in the first place after I published my article stinks.
This was never his real intention, the developer must also have to know what he started when he referred to my article in his own thread, that some fanboys/trolls then trying to attack me is only ‘logical’. He has some forum history with his previous apps, so someone only can assume what happens if you post something in such a thread/forum.
I call that the bitch way, he even made it worse by saying I should have contacted him before I write something. That’s an attack against free press speech and any blogger/website.
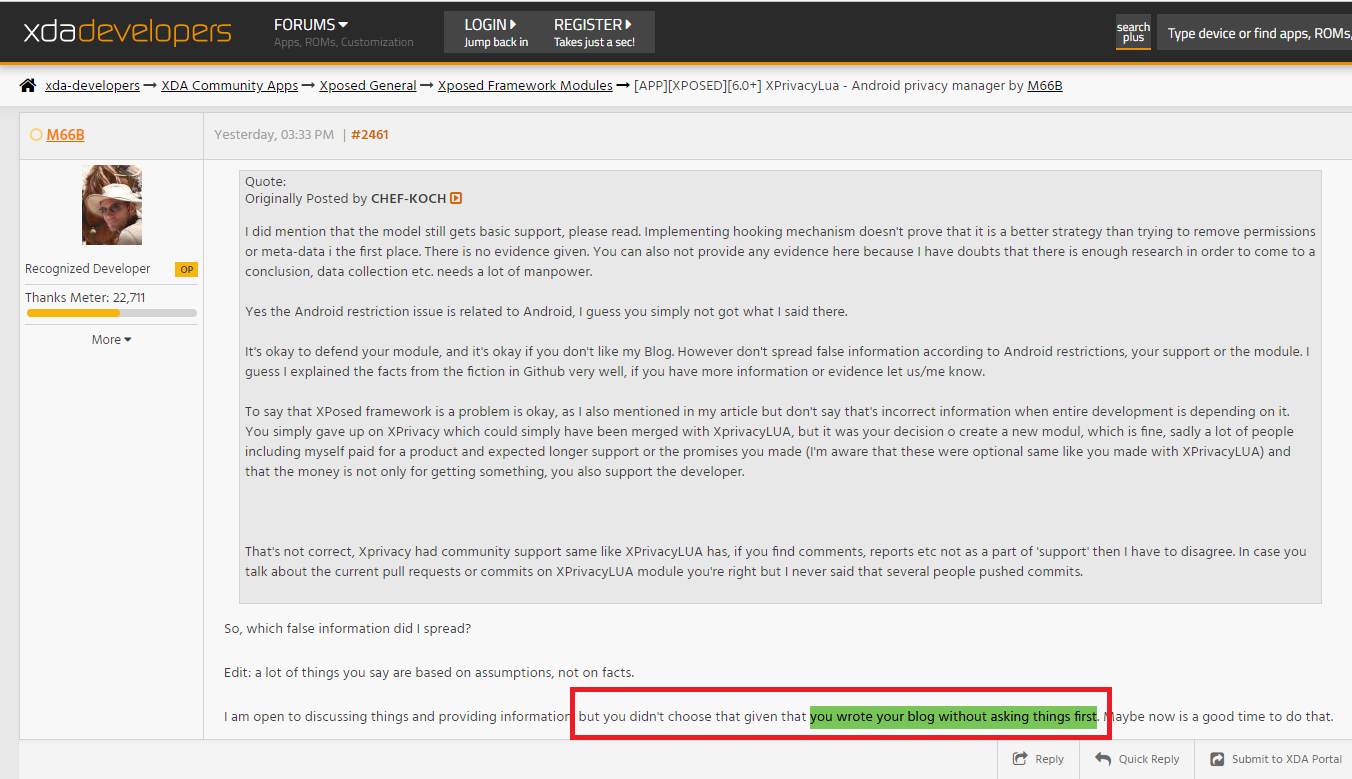
This screenshot and the developer’s statement shows he like to suppress your opinion/article because he expects that you get in touch with him first. This is ridiculous, he doesn’t even have the guts to contact me, he communicates still (after I closed this case already) in his fanboy thread – pointless. It’s like bringing valid arguments from Apple in a Windows-only forum, you just don’t do it because there is a reason why it’s called Windows forum.
“A lot of things you say are based on assumptions, not facts” – XprivacyLUA is FUD only and based on assumptions without any proof given on GitHub, XDA or on any other place. It’s wrongly advertised as ‘protects your data’ without any further explanation. The only one which is spreading FUD is XDA directly and the developer himself, which clearly things he can do things better than hundreds of Android, Tor etc developer. If it would be that easy why isn’t there a Windows, MacOS, Linux etc app to fake all data?
Facts about XprivacyLUA and his Developer
- There is no code audit
- The module wasn’t analyzed by experts to prove if a ‘privacy manager’ holds what it promises or if it is even a privacy-related ‘tool’
- The author doesn’t provide any evidence what are ‘real’ or ‘fake data’ exactly in detail and if it covers protocol leakage metadata. His source code only reveals that he used the research from Android Developers, ignoring the fact that attackers not using ‘genuine’ ways, cause they want to bypass it. You see that he is referring to it cause most of the code things are directly depending on it. E.g. the hooks using methods mention on Android Developers, which everyone could pick up in order to build strategies to defeat it.
- XprivacyLUA doesn’t cover every ‘privacy’ aspect, this is due several restrictions, Android’s Xposed ones or due protocol limitations. It’s not advertised or clearly mentioned in his front page. There in-consequence quotes but that’s it.
- Root itself is problematical, the module needs a rooted device, this is also not mentioned on the XDA front page directly or it also doesn’t mention any security problems which are coming once you decided to root the device. The front page or all of his other pages simply copy & pasta the links to GitHub, a normal user doesn’t even understand the source code, is interested to review it (due lack of knowledge, interest, time etc).
- M66B is clearly not a security expert. He is someone which claims to know a lot without giving any evidence, that what he says is true. In fact, he refuses to give evidence cause there is none. The code itself is no evidence as long it wasn’t tested7audited/reviewed otherwise this is just a pure claim based on no facts.
- He is a liar.
- He is in-transparent and there the open question regarding about his development. On the XDA front page, it say’s it’s a work in process product and on the GitHub repo it says all ‘features’ are integrated. What can we believe, sometimes it’s work in process and sometimes everything is done? Reminder: Every software/module is work in processes as long support is given.
- He might attacked me or at least some of his member. it’s a toxic community. I not even got an apologies for his or the actions of his community.
- He mention donations on the front page twice, instead of giving more facts, details etc on his module. He literally advertise his FAQ/GitHub as ‘fact’. Sure Google, Facebook etc also pretend they’re good. Referring to their own stuff.
- The developer can’t handle constructive criticism, instead he says other (or in this case I should) fix or contribute. Even if there is no Issue ticket option given. The also said that there will be no GitHub ‘issue ticket’ support without going into details. Btw: You also can block pull request or limit the repo.
- XprivacyLUA is depending on the Xposed Framework development process, my previous argumentation that it’s dead in the water is correct. Not everyone can use Xposed and it’s framework isn’t stable to deserve a overall recommendation. That it has it’s issue is simply a fact. However, I’m aware that every app has it’s issue but I not use this as argumentation in order to say ‘it’s not my fault‘. M66B was aware of this before he coded XprivacyLUA, so to use this as argumentation is weak. Once Google blocks Xposed (already happen) it will be more or less dead. Trying to defeat a security mechanism which is designed to secure you devise only shows how shockingly unaware the developer is when it comes to security relevant topics. It’s a fight against a windmill. It’s a matter of time, which I admit here but to use more apps break more things in order to get ‘privacy’ needs proof. Some malware is only activate if you’re on a rooted device or explicity designed to abuse root. This is also a fact.
- An attacker will pickup the source code in order to build strategies to defeat XPrivacyLUA. That’s not mentioned, I’m aware that this is a common problem but there is no code validation/binary validation given in order to at least very signatures etc. which would be the minimum.
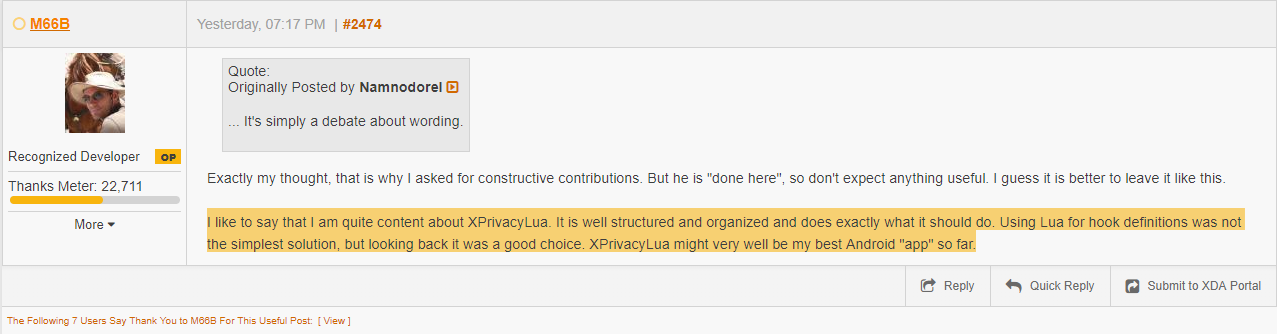
His arrogance seems at a real high-level, yet he refuse to contact me, other people need to defend his product. As you clearly can see here. Another member (which is unclear how he is involved in all this) called Namnodorel seems to speak and writes in his name.
Still no evidence given after several attempts
The developer still rejects to give any evidence that faking data provides any security benefit. He could do this on a real-world example and upload it on e.g. YouTube so that people can verify/test it.
He indirectly says every other security project would be wrong and his way would be correct. Tor Browser or other Anti-Fingerprinting mechanism are designed to remove traces or to avoid leaking data, they also offering more or less solutions to opt-out from traffic analysis. According to M66B his Xprivacy Lua module can fake or hide some of those data, which I seriously doubt since every protocol has meta data leakage, this however can’t be injected or hooked in order to fake it. One example is WebRTC leakage which expose you behind a VPN. I and others wrote about this long time ago here.
Some restrictions are also not covered by XprivacyLUA which isn’t directly visible or mentioned. instead he says it’s well organized.
A real-world example would be that you Login into a website which collects and spy on you, according to the developer can be covered however, this is wrong since modern pages using JavaScript in order to monitor you. This would require to remove or prevent the specific API which fingerprints you, faking this output still submits data and these are unique which according to EFF, can be used to expose you. Since XPrivacyLUA isn’t an ad-blocker you still send data to Reddit & Co, if these data are faked or not doesn’t really matter since unique behavior on these pages are also captured like what you liked, clicked etc. This is cannot be faked with any tool. The better solution here is to block the request so that no data (faked or real) can be transmitted. The developer of XprivacyLUA things that faking data is an answer, which is true, it doesn’t protect you against tracking itself nor does faking the fingerprint doesn’t allow several pages/app to monitor your activities.
Let’s assume the app fakes the screen resolution output in order to pretend that you’re behind a 1980×1080 screen on a 4″ device. This results in exactly the opposite, the one who is behind tracking will then check if his tools doesn’t work properly or why this is wrongly displayed. As a result ,he tries to check you or he implement even more mechanism to expose you. Even if you fake the same output for let’s say 2000 devices which are using exactly the same fake data, it would be easily to expose you because this is suspicious. And with some research, the attacker can then come to the conclusion that these data are used by Tor or an app etc. There is no workaround for this, XprivacyLUA also can’t workaround this, this however is often used in order to geolocation block you or blacklist a specific pattern/behavior. This also doesn’t affect VPN users, some software is also be blocked.
XprivacyLUA also doesn’t offer any protection against ARP spoofing, or EUI-64 sniffing. An example is once you use IPv6 (which isn’t properly configured) you expose your real MAC address, faking your IP when your Mac Address is been revealed is rather pointless, the ‘privacy Manger’ solution does nothing in order to prevent this.
- DRM is not hookable/injectable if it’s coming from the hardware Xposed framework has no low-level access
- XposedPrivacyLUA doesn’t inject JavaScript based fingerprints, it’s not possible because XPL hasn’t access to isolated Browsers or sandboxes.
- XprivacyLUA doesn’t prevent, detect or manage hardware based backdoors. It’s not possible for the Xposed Framework to get low-level access. An example is if you flash a compromised booloader/firmware.
- XposedLua can be defeated and bypassed via TWRP.
- Rooting the device is a bad advice, especially if the documentation/FAQ doesn’t tell anything about negative consequences.
- XprivacyLUA doesn’t prevent anything from stealing data, faked or not. A malicious app can still grab your data, like e.g. WhatsApp database etc
- It doesn’t provide any ‘privacy’ relevant function in order to encrypt your device or files not is the framework compatible to it.
- XprivacyLUA doesn’t prevent meta-data leaks cause it doesn’t change protocol relevant things and it doesn’t offer any ‘help’ here.
- No MITM protection. Faking data doesn’t protect against been exposed by someone which tries to get your data. There is no layer of protection here added.
- XprivacyLUA can be crashed with other root apps, it don’t contain any protection mechanism against this, an attacker can crash the app and inject malware which makes the entire point of using the module pointless.
Suggesting to root your device in order to install Xprosed/Magisk for XPrivacyLUA is dangerous and not mentioned (for a reason!)
Root is dangerous in the wrong hands, it’s a fact. More than the risk of malicious apps and warranty of course, another problem will be annoying bugs after you root and put a custom ROM on the device (in most not all cases). Many important things could suddenly not work. For example, I had a issue with a custom rom, all worked fine except Wi-Fi, another custom ROM was not recognizing my second sim, this is however a custom ROM thing. Of course, this is only one example in order to show that custom roms can be problematically, especially with drivers and features because it needs to be merged with AOSP changes.
Root itsel defeats the security model that’s been in place for many years. Applications are meant to be run with non-administrative security so you have to elevate their privileges to modify the underlying system. Hacking Android Apps Using the Xposed Framework is possible, another example is given with more details here.
Dangerous of rooting your device, some research papers:
- http://downloads.hindawi.com/journals/misy/2018/6020461.pdf
- https://www.researchgate.net/publication/260343583_Rooting_Android_-_Extending_the_ADB_by_an_Auto-Connecting_WiFi-Accessible_Service
- https://www.princeton.edu/~slaughtr/Articles/Root.pdf
- https://seclab.ccs.neu.edu/static/publications/issta2017sifon.pdf
- http://www.ru.nl/publish/pages/769526/kremers_-_security_evaluation_of_mobile_device_management_solutions.pdf
- https://securelist.com/78648/dvmap-the-first-android-malware-with-code-injection/
- https://forum.xda-developers.com/xposed/xposed-faq-issues-t2735540 (the developer of xposed framework itself says it “other ways of modifying your phone are also open to malicious coding“.
Recommenced others to root your device in order to install another Framework to get a module working is dangerously and the Xposed Framework itself also never got an independent audit. Another Xposed app can simply bypass every function of XprivacyLUA once the user applied it, which is possible because you can’t inspect or assume everyone is an expert. An infected app which seems legitimate can then infect the bootloader itself, or bypass Xposed Framework or manipulate it, this is an realistic scenario. The Developer doesn’t show based on his code how he would prevent this, right it’s not possible.
XprivacyLUA also has no protection mechanism in order to protect itself from been shutdown by other apps with higher rights, cause it’s not possible.
Fingerprinting
I would love to see how an application defeat all this.
-
Hardware Fingerprinting Using HTML5 (arxiv.org)
- Is it possible to defend against browser fingerprinting? (panopticlick.eff.org)
- Remote OS detection (nmap.org)
- POTARC (github.com)
- Fingerprinting specific API’s (randomwalker.info)
- Crossbrowsertracking (yinzhicao.org)
These are only some examples of course, the point here is that one single person can’t defeat everything and even bigger projects like Tor with lots of manpower behind have their problems, that said Tor alone is not 100% secure. Compared to XprivacyLUA the Tor Project did mentioned this clearly and explain the possible risks. XprivacyLUA doesn’t even document or explain half of it negative consequences, this is also a fact. It’s true that some things are mentioned but it’s not enough.
Developer shows disrespect to his own community
- From his XDA front page quote “You can report any problem you have here. There will be no issue tracker on GitHub.” Even if people only helping on forums by giving debug infos etc it’s is some kind of support. Some seems to love the module, they provide their debug/error data, and without it the module would’t be as good as it maybe (?) is.
- Xprivacy itself got community support, which I original was referring too, but M66B quote it in his on context.
- Ignoring the Xprivacy point, the translation page for XPL does has contributors. It’s unclear if you even can contribute on GitHub (honestly I didn’t tried if the repo was restricted [but M66B could have changed the option in the meantime, difficult to prove I must admit]).
- The linked GitHub page with contributors exclude translation, donations etc. which is also definitely support.
Closing Words
M66B is not an security expert and his stamens are dangerous, naive and wrong. On one side he advertise his product as ‘security’ product (calls it ‘Privacy Manager’) on the other side he says it’s just an Xposed module which offers some hooking functionality. These two mentioned things are different, people which are not involved into the security relevant topics might see this as an solution in order to prevent several things. This is how you basically catch and create myths. It’s not clear what ‘privacy’ exactly in XprivacyLUA mean and it’s not well written down. The interpretation has lots of room here. There not much downsides mentioned regarding root, there is also nothing mentioned about the warranty on the front page and there more such curious statements given from people which are not involved into security relevant topics, discussions etc.
XprivacyLUA is not a privacy application (it claims to be one) and this has to be said. What the module does is it reduces the possible attack surface without providing more details based on real-world examples. It’s questionable if that has any security relevant benefit, the developer only claims his things but doesn’t provide any scenario here, how it prevents let’s say that Facebook gets your real like your Mac address. When you come with some security relevant questions and doubts the developer seems ignorant to admit things, instead he states “make a commit yourself”. This is not the proper way you handle it, this doesn’t help at all, and the front page or the GitHub repo still wasn’t changed in order to address the things I already submitted on XDA.
I had some respect for this developer, but that changed immediately after I discovered that he lied to me. I question his reputation in general here, I also won’t believe he did any proper research, he said he did ‘a lot’ (what is a lot?) but without going into further details or list it on his pages. Visiting Android Developers page in order to see how Android’s permission system works is an example and not research. It’s a short way to see it one one side, ignoring the fact that everyone with Internet access and some coding skills are also able to come up with something in order to defeat Android’s given restrictions based on public information, the most popular application here is LuckyPatcher (which XDA itself wrongly classifies as Warez).
The shameless reaction I got after publishing an article shows that some people getting angry when you say something against their favorite product, this reminds me on AntiVirus times when people constantly defended their loved products (and they still do) – ignoring all facts and possible security relevant question. Closed minded people.
Bokhorst seems a developer which defends his products even if I clearly showed that there are weaknesses. The module itself doesn’t deserve a classification as ‘security manager’ or a ‘tool’ which protects your data/Android. He’s also inconsistence in what he thinks about his own product, sometimes it’s a privacy or security relevant product sometimes it’s just another Xposed module with some hooking ability. These things are separate topics, the fact that there is no audit or review because it’s an app which gets a lot of changes only prove that my statement is not incorrect since no one really took a closer look into it. The source code however is provided in order to do so.
I can’t recommend to use a any of those Xposed module product in general. Especially not from someone which lies in order to defend his own product, or someone which ignores some important points or is willingly to give evidence about the claims.
The PrivacyLUA developer says it’s the (his) “best Android app” when it comes to privacy (cause he implemented that here is no better app out there). I seriously have my doubts about marketing promises like this, history told us other things. A VPN might help the same or even more here cause the layer of security it offers is in my opinion in a lot of cases better (no MITM, leakage etc). But even a VPN is not 100% the answer – I have to admit this.
I think the whole story speak against M66B and his application. It’s wrongly advertised, the documentation is incomplete. He refused to communicate with me directly, instead he started a drama on XDA. At the end I have to pay this (thanks btw). Afterwards, he said because I stropped the conversation that I had nothing more to offer, true – I don’t offer help to liars or pseudo experts cause it’s worthless to talk against whole fanboy community.
Marcel Bokhorst already decided to stop the conversation when he lied, I see no point to argue against FUD or fanboy’s – it’s my lifetime I not need to prove anything btw cause I’m not the one which claims to ‘secure’ Android. Instead I was so kind and did this in the meantime, I showed it doesn’t help the way Bokhorst think it helps. A serious ‘manager’ application would require a massive amount of research and thousands of hours of work in order to build something which truly offer a layer of security. I have reasonable doubts that a single developer can ever do this without helps (remember, no XprivacyLUA commits from other people [yet]).
M66B also not mentioned or told us the entire truth, he seems very fast unmotivated, blames other things for this e.g. Xposed Framework development – but this was all known from the beginning when he started. I moreover think it’s money which is the real reason. This makes me question his true intention, however the money argumentation is difficult to prove since no stats are given in order to see how many people has donated or purchased the app and how many people liked to get their money back. The entire project is for this what it advertised not well organized, there is some lack of information and we simply need to trust a his words.
If someone actually found (based on current findings) any real evidence, let me know I pay $1000 dollars for reasonable research and proof. I stand to my word.
You should ask yourself:
- Why you should support a developer if he is a liar and in-transparent
- Why you should install a module which doesn’t add a real ‘security’ benefit to your device when no evidence or code audit or specific example was given?
- Why the developer refuse to give any evidence (cause he can’t, period). If he can, show us all a real-world example how you for example defeat Facebook tracking/spying etc after you logged in into the page. I would love to see that, especially because you can’t build something if you haven’t fully understand what it can collect or does actually detect. Because M66B says he needs no research or research paper). I guess his pure arrogance is speaking.
- Why a someone recommend to root your device and install an module and app which can be bypassed/exploited anyway and this easily within Xposed / TWRP or Android itself. It’s like saying use my module cause Android’s mechanism are weak but ‘forget’ to mention that his module doesn’t solve the problem at all.
- Why he did not gave no apology after I debunked his lie or for the action of himself of his community. It’s unclear if he is behind the attack one member of his community/xda – but I’m naive and do believe it’s a troll/fanboy and not the developer himself.
- Someone tries to suppress my right or free speech.
- Why this developer needs other members to defend his product?
- Why do you want to support someone which change his mind about his own module each time you mention ‘privacy’ with lame excuses even if the module is clearly all over the place advertised as ‘privacy manager’?
M66B lost all of his credibility. He literally defends his product with nothing but claims which makes it even more hilarious. Good projects like e.g. VeraCrypt does proof that their product is secure and hold what it advertise – so why can’t he? Ignorance, unwillingness to cooperate, lies, defending argumentations make it impossible to give him any more attention than he deserves.
I uploaded all pictures/conversations etc in a Mega folder in case he or a moderator tries to manipulate or edit something.
My Blog will be monitored now in order to prevent more damage.
Resource
- Fighting Cyber Security FUD and Hype (securityweek.com)
- Security Through Confusion – The FUD Factor (blog.sucuri.net)
- FUD Sells a lot of Security Products | Evan Francen | TruthsInSecurity (truthsinsecurity.com)
- FUD and Cybersecurity Marketing (phoneboy.org)
- FUD or Fact: The Role of News Media in Security – Security Intelligence (securityintelligence.com)
- Flashback: Kaspersky Spreading That FUD Again (rixstep.com)
- Data masking (wikipedia.org)
- Hooking explained: detouring library calls and vtable patching in Windows/Linux/MAC-OSX (ntvalk.blogspot.de)
- SPOOFING CYBER ATTACK DETECTION IN PROBE-BASED TRAFFIC MONITORING SYSTEMS USING MIXED INTEGER LINEAR PROGRAMMING (bayen.eecs.berkeley.edu)

12 responses to “Shhh don’t say a word against XprivacyLUA or else…”
Not an IT guy here but do you mean in other words xprivacylua is not entirely doing what it is claiming and it made no difference if we install it or not and if we install it we risk more because it might take our real data and sell it to companies since faking data can be bypass by the apps?
If it is, do you know any alternatives? Preferably open source?
And what do you think about his other product netguard which is open source? Does it have security flaw too?
LikeLiked by 1 person
NetGuard is from the same developer.
The problem with application ‘security’ is that they are mostly placebo, written from people which trying to make money by scaring people to advertise their own products. This works since over 20 years for the AV industry and now it seems to work for Android as well. The Android VPN interface by itself also has weaknesses which are only fixed on higher Android versions (8+). To recommend all over the place to use VPN when the interface also has weaknesses is problematically in my opinion. If there doubts about my words I would upload a research paper which demonstrate how Android’s VPN api can be bypassed. The problem is that most apps never got a serious audit which verifies if it’s really a ‘security’ wise a good decision to use it rather then using integrated Android internals.
Whenever a developer refuses to give evidence that it works like he claims then you should question the developer and all of his products. There tons of examples in which case XPL doesn’t work, for example using encrypted GPS, you can inject or hook or try to manipulate it’s content it will always fail. There tons of more examples. I’m not going to say that the app or it’s ‘addons’ which the user can install in order to hook xyz doesn’t work but there are limitations coming from Android itself and from certain protocols which doesn’t allow you to manipulate it’s content, besides other apps might easily detect his application with a simple package name check in order to behave differently whenever xposed or XPL is installed.
The developer argues that ‘he does something’ which I really question here, I and other people doing a better job bringing security features for ALL people directly into Android while he makes money + advertises his product as ‘security manager’ which is nothing but marketing strategy. If he really want to do something then he should work with me and others which directly contributing into the Android source code in order to fix weaknesses directly.
Xposed framework itself has weaknesses – if you won’t believe me, just take a look into the xposed github repository and it’s issue tab. Xposed is also not meant to be something which improves your OS security and it was never advertised as such thing. It’s also questionable why someone should root his device in order to install xposed and a module I see this as critical, rooting your device basically breaks the integrated security mechanism.
LikeLiked by 1 person
Close your blog and stop your lies, shithead!
LikeLike
CHEF-KOCH, where are you live ? I hope not in USA. No matter , you are lucky guy because M66B is not from USA. Else he could sue and get a large monetary compensation for what you’ve smeared here.
LikeLike
I tried to read this article but i failed in the half. Dear author please stop write nonsenses and hate. It is not possible to read. Do you work for secret services and want to destroy protection private initiatives? Better close your blog and do not write anymore.
LikeLike
“Protection” – Marketing is really strong isn’t it?
LikeLike
Are you David Nagel? Well, wo know where you live now…
LikeLike
I’m not David Nagel, that’s for sure.
LikeLike
Thank you CHEF-KOCH
Your articles are always interesting
LikeLiked by 1 person
You have some serious problems. Go and see a doctor! Honestly!
LikeLike
interesting article
what do you think about this software?
it’s safe?
https://cryptomator.org/
https://github.com/cryptomator
thanks
LikeLike
I’ll consider to review CryptoMator in the future. The program itself is a great open source alternative to BoxCryptor.
Interesting material I can link you:
* https://community.cryptomator.org/t/has-there-been-a-security-review-audit-of-cryptomator/44
* https://cryptomator.org/audits/2017-11-27%20crypto%20cure53.pdf (audit speaks positive for CyptoMator and some mentioned things already got fixed)
* https://www.cryfs.org/comparison (maybe start with this first to get an overview)
CryptoMater itself is easy to use but has some problems in the usability, one example is that it might has problems with special characters then you might see mounting failures, however this can still be fixed. If you asking me what my suggestion is VeraCrypt vs. CryptoMator I would say go with CryptoMator because VeraCrypt containers can not be opened on more than one computer at the same time. But if you don’t need to sync your content across several devices/cloud’s etc I say stick with VeraCrypt. CryptoMator is more designed to be an alternative to BoXCryptor and the entire ‘cloud’ problem, so it’s more designed to fill this need.
I hope this helps you.
LikeLike